A post-mortem of a contained ransomware incident. Learn how architectural blast-radius control, identity-first policy, and immutable recovery turned a potential catastrophe into a minor operational blip.
Quick summary (for busy readers)
- Shift from Perimeter to Blast Radius: Assume the "hull" will be breached; design independent pressure vessels to ensure the ship stays afloat.
- Identity is the New Control Plane: Moving from network ACLs to Zero Trust Network Access (ZTNA) and Identity-Aware Proxies (IAP).
- Immutability is Non-Negotiable: Use WORM (Write Once Read Many) storage to defeat "time-bomb" ransomware.
- The Goal: Optimize for Mean Time to Contain (MTTC) and minimize the Blast Radius Ratio.
The Scenario:
When the ghost admin met the malware
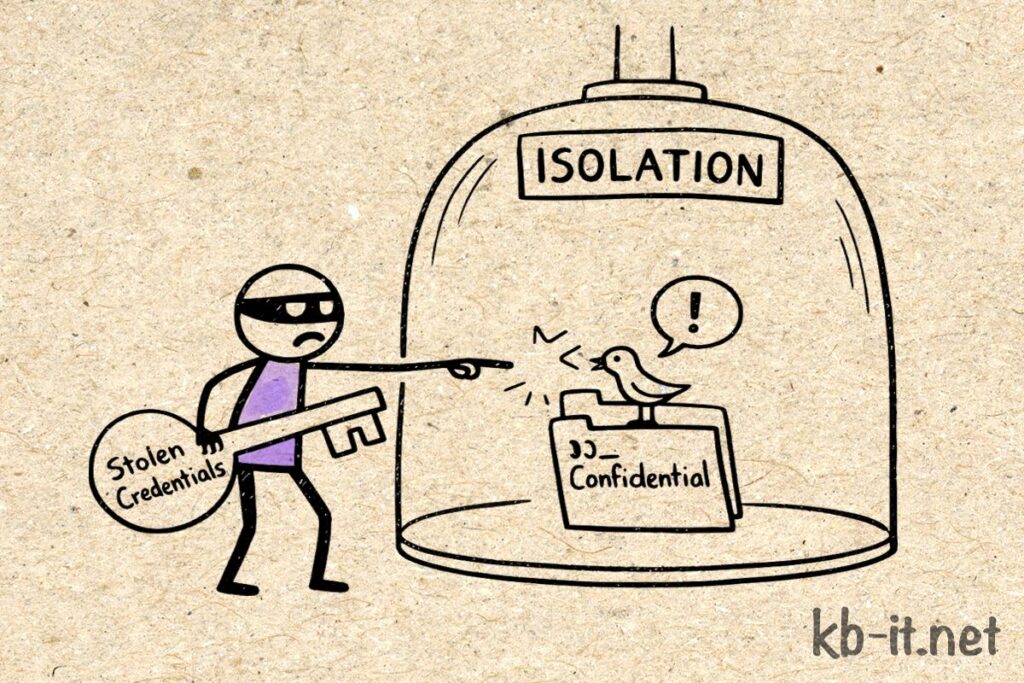
A sophisticated session-hijack targeted a high-level administrator. The attacker expected the keys to the kingdom, but they encountered an architecture designed for “the ghost admin.“
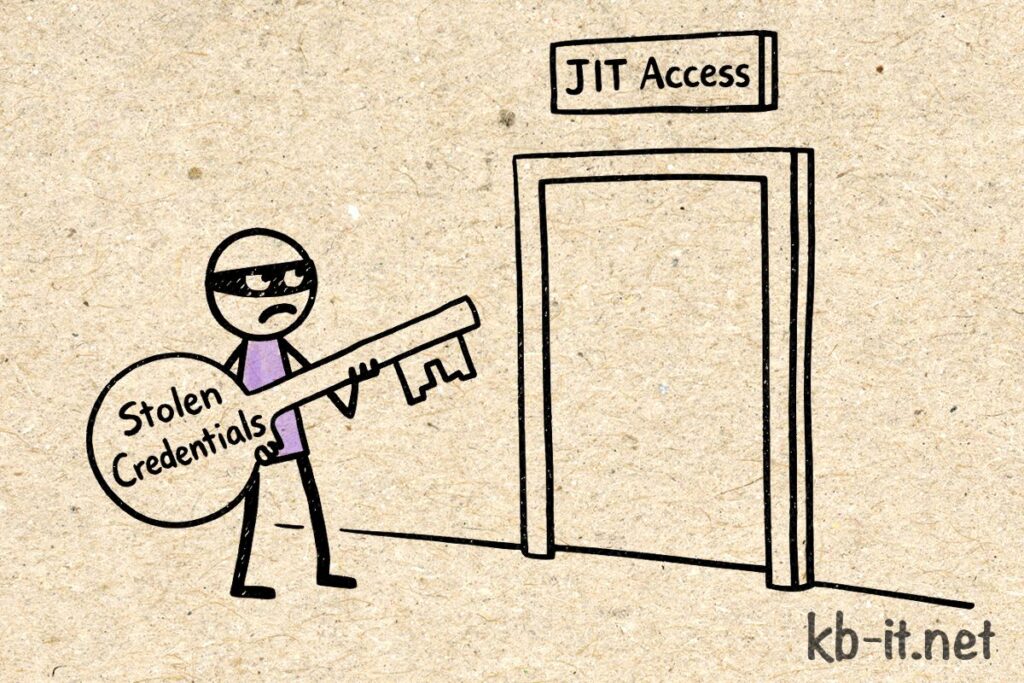
Even with valid credentials, the attacker found an account with zero standing permissions. To execute any meaningful change, they would have needed to trigger a Just-In-Time (JIT) elevation request, verified by a hardware token and a second human approver. While the attacker sat idle, looking for leverage, a Digital Canary a hidden honeypot share named confidential_data triggered an automated isolation playbook the moment the first file was touched.
The attack was contained before a single production byte was encrypted.
Why These Controls Work (The Submarine Strategy)
A modern submarine doesn’t survive a hull breach by hoping the hull is unbreakable; it survives through independent pressure vessels.
- Microsegmentation as a Pressure Seal: Move away from "Layer 3" thinking. By using Business-Capability Mapping, ensure that a breach in the Marketing segment cannot physically reach the Production Database segment.
- The 1:1000 Blast Radius Metric: In a flat network, 1 compromised device = 100% exposure. Your goal should be a 1:1000 Ratio: ensuring that any single point of failure exposes less than 0.1% of the total estate.
- The Immutable Time Traveler: Attackers often "dwell" for 60+ days to rotate out clean backups. By utilizing WORM storage with a 90-day retention lock, you deprive the attackers of leverage. Instead of "restoring from yesterday", the system enables you to time-travel back to a verified, immutable state in under two hours.
Practical Architecture Patterns & Trade-offs
| Pattern | The "Why" | The Architect's Trade-off |
|---|---|---|
| ZTNA / IAP | Decouples access from network location; high-fidelity signals. | High OpEx: Requires deep integration with a robust IAM fabric. |
| Microsegmentation | Hardens the internal blast radius; stops lateral movement. | Initial Friction: Requires a canonical service inventory and identity model. |
| JIT / Least Privilege | Eliminates standing "Admin" targets for credential harvesters. | Operational Latency: Requires automation to prevent "Security Fatigue" in staff. |
| Air-Gapped Recovery | Ensures the backup control plane is separate from the domain. | Complexity: Demands rigorous, automated recovery drills. |
Common Mistakes
That Let Ransomware Win
- The "Crunchy Shell, Soft Center" Network: Relying on firewalls while leaving SMB/RDP wide open internally.
- Shared Fate Backups: Using the same Active Directory credentials for both production and backup storage.
- Static MFA: Failing to account for modern session-hijacking that bypasses simple 2FA.
- The "Shadow" Recovery Plan: Having backups but never testing the Recovery Time Objective (RTO) for the Active Directory itself.
Pro Tips:
The Executive Checklist
- Deploy "Digital Canaries": Create honeypot files and shares that trigger immediate isolation alerts.
- Enforce Device Attestation: Treat unmanaged or "unhealthy" devices as high-risk, regardless of the user's credentials.
- Audit the "Blast Radius Ratio": Map your network and ask: "If this node is compromised, what is the maximum percentage of data it can touch?"
- Automated Response: Don't wait for a human to read an alert; automate the isolation of the workload the moment mass-file encryption behavior is detected.